This week I have been kept busy attending a Webex-based online delivery of Cisco’s Data Center Network Infrastructure 2 (DCNI-2) course. This course is basically all about the Nexus 7000 and 5000 platforms, the operating system (NXOS) and all the fun you can have with it. It has also turned up a few interesting side discussions, some of which I’ll share in this post.
I thought it might be worthwhile though to talk a little bit about the delivery of the online course, the materials, the scope of the course, and whether or not it’s any good. I’ve not taken a five day Cisco course online before, so this is an interesting experiment for me.
Course Outline
To give a very broad overview, this course covers Nexus 7000, Nexus 5000 and Nexus 2000 (FEX). The course I’ve been attending was delivered by Firefly, and I’ll reproduce their course summary in case it gets updated on their site between now and whenever you are reading this (I hope they don’t mind):
After you complete this course, you will be able to:
- Describe the features of the Cisco Nexus 7000 chassis, Supervisor Engine, and line cards
- Describe the architecture of NX-OS
- Describe the Connectivity Management Processor
- Configure switch management features like Call Home, Logging, AAA, RBAC
- Use configuration checkpoints and rollbacks
- Configure Virtual Device Contexts
- Configure Layer 2 and Layer 3 services
- Configure Overlay Transport Protocol
- Describe FabricPath
- Configure NX-OS Process Recovery
- Configure NX-OS Supervisor Redundancy
- Configure Hardware Rate Limiting
- Configure Quality of Service
- Configure traffic integrity features and Control Plane Protection
- Configure access and admission control
- Use SPAN and Ethanalyzer to monitor traffic
- Describe how FCoE operates within SAN and LAN environments
- Describe the ASIC-level architecture of the Cisco Nexus 5000 switch and CNAs
- Configure the Cisco Nexus 5000 in switch mode and NPV mode
- Configure the Cisco Nexus 2000 as a remote line card
- Configure Virtual PortChannels
All things considered, it’s not a bad list of topics – definitely useful to you if you are going to be using Nexus hardware (and NXOS software) in your data centers. The first three days are focused on the Nexus 7k, and the subsequent two days are on the Nexus 5k. The Nexus 2k is covered in both the 7k and 5k segments, though definitely more so with 5k. You probably would not have guessed that kind of split by looking at the course outline, which seems at first glance to be 90% Nexus 7000.
There is definitely more material to go through here that at first meets the eye – things can move very fast, and if you do not already have a good understanding about the basic technologies that are being covered, it’s going to be challenging. This is not, for example, the moment to realize that you have never used Cisco’s Modular QoS CLI (MQC), or that you have little to no knowledge of deploying Fiber Channel (ah yes, that would be me then). In the case of FC, the course did cover the basics to try get the class up to the same level, but it was an awful lot to take in at a very fast pace and I suspect anybody who works regularly with FC will tell you that 30 minutes is not enough time to actually understand much.
The Nexus (and NXOS) is very different to previous Cisco switches, and there are a lot of nuances to configuring them that are simply not obvious if you just sit down and start typing. The course content highlights many areas that I believe are very important if you are considering deploying this hardware, and it’s information that I haven’t seen out there in such a compact form anywhere else.
Course Materials
As is normal for Cisco, the course materials comprise a few books of course slides and notes, and a separate book of lab exercises. However, for this particular online course (which I believe Cisco is paying for), Cisco are being green (or saving themselves some money?) and are delivering the course materials to us online rather than mailing heavy hard-copies to us. The delivery mechanism therefore is Cisco’s eKit Viewer, which I had not used before.
eKit Viewer is a Microsoft Silverlight application that manages the download and display of rights-managed content, allowing Cisco to deliver purchased materials to you (and only to you), as well as being able to enforce timeouts on the content. Our course material, for example, will be deactivated in 12 months’ time. I’m torn on this issue – on one level, the idea that the material can be updated any time is good. On the other hand, in 12 months I’ll still be using Nexus hardware, and a great reference resource is being taken away from me – whereas if I had the actual books, I’d have them forever. eKit does allow you to print the books, but reports from others in my class indicated that they had problems printing the larger of the books, apparently due to the size of the print job. There are over 400 pages of slides and 300 pages of lab workbook; if you do choose to print them out that’s over 700 pages (350 if you are as green-minded as Cisco and you double-side them) of unbound paper. I suppose I could buy some binders and hole punch all of the sheets, or I could go spend a fortune at somewhere like Fedex Kinko’s to get it printed and spiral bound, but then why should I have to do that? In true “ePUB” style, by the way, the printed copies will have your name and CCO ID as a big ugly grey watermark plastered diagonally across every page (not annoying at all when you want to study, oh no). I understand the need to protect electronic content, but there’s a fine line between protected and unusable (cf. Apple, Sony, etc). You are limited to four printing attempts per module, so my advice – for what it’s worth – would be to initially print to a PDF driver. I’m quite sure this is not what Cisco had in mind, but it did appear to work for me and means I might actually be able to read my (heavily watermarked) material on a device other than the PC that my eKit Viewer resides on, so while I can do it, it’s a firm thumbs up from me for this option. I should add that each module has to be printed individually, which is a tiresome process.
eKit Viewer provides the ability for you to highlight text, underline, strikethrough, add sticky notes, use e-ink style drawing/writing tools, and bookmark pages as required. Ultimately the problem I found is that when you are viewing the online presentation or working on labs (more on the labs later), it becomes very frustrating to fit everything on the screen – remember, you are constantly flipping between the lab directions and the lab equipment, and unless you have a very high resolution screen (or multiple monitors), this is a true annoyance and I found it was to the detriment of the overall experience; I spent too much time resizing windows and dragging them half off the screen in order to be able to have a telnet window up at the same time as the lab notes.
While eKit’s rights management allows for printing, it does not allow direct content extraction. That is, if you were thinking to copy a command from the lab guide and paste it into your lab router, forget it – you cannot copy content. Similarly, if you try to use the standard PrintScreen functionality, you’ll discover that it doesn’t work and you will have an empty paste buffer. Now, I don’t mind particularly if eKit wants to protect itself and its content – but this protection doesn’t just block screen grabs of eKit, but blocks all PrtScn usage, whether or not eKit is visible on the screen. This is out of line – eKit should not be interfering with the rest of my workflow. Still the good news is (until inevitably they find a way to block it) that the standard Windows 7 snipping tool works just great so long as you save it to disk rather than expect it to be in the paste buffer. *cough*
Minor irritations about eKit usability include that chapters are not named when you go to select them. Here’s a view of my current eKit catalog:
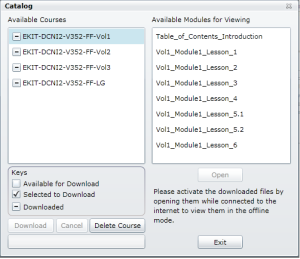
The four ‘courses’ on the left hand side are the three volumes of slides and one Lab Guide (LG). On the right hand side I can select which part of the book I want to read – but the only way to know what is in each chapter is to open the Table of Contents chapter, find the part I need, then go back to the catalog and open the lesson directly. Not impossible, but definitely suboptimal when the instructor says “Ok, next up we’re going to look at QoS on the Nexus 7000“, and worse still when I want to run through specific slides again. I should add that not only is the the Table of Contents within the book itself not hyperlinked to make jumping to the right chapter simple, but the page numbers that eKit reports in the page previews down the left hand side of the window do not align with the numbers on the actual page images, so while you can scroll to get close to what the ToC says is the destination page number, you’re always a few slides away from where you want to be.
My final beef with eKit is the authentication / validation mechanism. When you get content, it’s through the Cisco Learning Network Store, where you activate and/or pay for your desired content. The content should then automagically appear as being available for download in eKit itself. In order to this to happen, eKit attempts to connect to the Internet each time it starts up. After a quick software update verification, it establishes an SSL connection and presumably then confirms what courses are valid for your eKit instance – and I would assume also confirms any that are due for removal (will let you know in a year’s time!). This is great except when it doesn’t work. I had downloaded the eKit material in the week prior to the course beginning, and had re-validated that I could read the content on the Friday just before. Monday morning, the first day of our course, I opened eKit to find that I had no content, eKit showed as unactivated (i.e. not related to my account), and it refused to reactivate using the codes I had, citing an exception error. The same was true for everybody on the course. Three hours or so later, Cisco had fixed the issue and our material reappeared, but not before the day had been disrupted significantly. To be fair, Cisco’s eKit team were fast to respond to the report and notified me when it was repaired, but it’s again something that couldn’t have happened with actual books.
My conclusion on eKit is that while it’s a nice idea and very environmentally friendly, it really isn’t a good substitute for having the proper slide handouts and lab workbooks on my desk where I can easily make notes while still having the trainer’s slides, or the lab sessions on the screen. Come back to me when I have a pair of 30″ high res monitors available…
Labs
The labs for this course are all online – after all, who wants to cart around racks of Nexus 7010 and 5010 and ESX servers around with them? Even if you did, you wouldn’t be able to power them on site, so really “hands on” is a bust. Incidentally, when I went to an in-person version of this course before (long story, and I did not get to complete it), the labs were also all remote – so this is a normal delivery method.
The labs are pretty well set up – there are a few typos in the lab guide (more in the 5k section than in the 7k), but that just makes things more fun as you get to troubleshoot what happened. The equipment for the labs is reserved to align up with the lecture days, and the lab equipment is scheduled for other classes in different timezones as required to maximize return on investment. Access is using Remote Desktop Client (RDC) to login to a remote machine, then a web-based dashboard allows you to see the lab topology and device status, and allows you to connnect to the console of servers and to RDP to XP machines and Windows Servers.
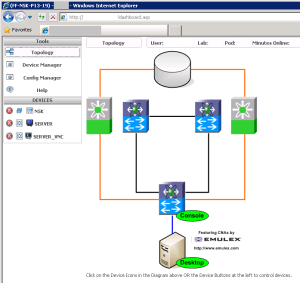
These virtual XP/Server machines then allow you to SSH to the Nexus devices once configured, run a TFTP daemon, run Cisco Device Manager, and so on depending on the lab setup.
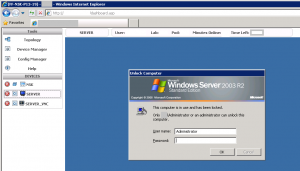
Everything is charmingly virtualized, and it’s a clever use of the technology. Depending on your login, the web dashboard will show different equipment – i.e. the first login connects you to a Nexus 7k lab, then under a second login, a Nexus 5k lab. Lab access is timed carefully – logins to the Nexus 7k lab expire after 3 days, and because of the time-sharing, the logins only function from 10am to 10pm or thereabouts.
The lab system is quite effective, utilizing VMWare ESX to power the test servers and XP client machines that connect to the lab equipment, meaning you have sources for traffic in the labs if required (even if it’s just a ping!), and devices with an HBA available to test FiberChannel.
The labs included for Nexus 7000 are:
- Lab 0: Cisco Nexus 7010 Configuration Baseline
- Lab 1: Cisco Nexus 7000 Hardware Platform
- Lab 2: Managing System Configuration
- Lab 3: Configuring FabricPath
- Lab 4: Configuring VPC
- Lab 5: Configuring Routing Protocols
- Lab 6: Configuring OTV
- Lab 7: QoS on the Cisco Nexus 7000
- Lab 8: Security
- Lab 9: Troubleshooting the Nexus Control Plane
And for Nexus 5000:
- Lab 1: Configuring the Switch for Administrative Access
- Lab 2: Configuring the Cisco Nexus 5000 Switch for FCoE Connectivity
- Lab 3: Configuring the Cisco Nexus 5000 in NPV Mode
- Lab 4: Traffic Engineering
- Lab 5: Configuring the Nexus 2000 as a Remote Line Card
- Lab 6: Configuring Nexus 2000 with VPC
One thing that’s interesting to me is that the 7000 and 5000 labs have a slightly different style to them – I would assume written by different people/teams. The 7000 labs are classic Cisco “don’t think just type” labs, where you pretty much follow the instructions but don’t have to think too much. The 5000 labs however start each section by saying something to the effect of “if you want to have a go at this the hard way (i.e. without help) here are the things we want to achieve” – and if not, carry on and on the next pages we have the typical step by step brain-disengager labs. I do believe that the entire lab workbook should be done the 5000 way – let us try and think the solution through and see how we do before just handing the answers over on a plate. I’ve had f5 training before that followed a similar process – they would give you 3 or 4 step-by-step labs, then the 5th (Advanced) lab would be one with no guidance whatsoever – just a list of requirements and a way to test if you got it right. That’s a really fabulous approach as it holds your hand, then makes you reinforce what you learned. In my opinion Cisco would do well to learn from f5’s example in this regard.
Little whines aside though, the lab concepts are pretty good, and the actual implementation of the remote labs is pretty clean. No, it’s not hands on in the physical sense, but it’s a real device with real (virtualized) servers hanging around them in addition to the lab infrastructure itself. Good job on this one.
Personal Comments
I’ve very much enjoyed the Nexus 7000 and related NXOS content – it falls squarely into my comfort zone, and it’s just a new way of doing what I already know. The Nexus 5000 has been a much bigger struggle for me; not being a Fiber Channel guru going into this, I’m battling the technology the 5k supports as much as I am the actual platform. And of course, the configuration makes less sense to me immediately than I would like. I’ll definitely be going back over that material in my own time (using eKit ;-)).
But I Digress…
As much as the technical content has been interesting, some of the class sidebar discussions have been perhaps even more so.
My personal interest was aroused when discussing where the Nexus fits in to the overall product line. For example, you could argue that the Nexus 7000 is a natural progression for owners of Catalyst 6500/7600 switches; faster, higher port density, etc. Supposedly though Cisco does not see it that way and is trying to position it differently in order to protect its existing 6500/7600 business. Of course, if you need increased port density over what the 6500 can offer you, what choice do you have if you stay with Cisco? There have been rumors of a SUP/RSP1440 (or similar) finally supporting 80Gbps backplane connectivity per linecard for the last 3 years, but it has never materialized (hmm, 80Gbps per linecard – sounds like the Nexus 7000 linecards, doesn’t it?). For my previous clients, the 6500/7600 just didn’t cut it in terms of 10GigE port density and with a maximum of 40Gbps to the backplane, an 8-port 10GigE linecard like the WS-X6708-10G or even the 16-port WS-X6716-10G are just fanciful in terms of the level of oversubscription you open yourself up to.
This perhaps also explains why the Nexus 7000 does not have Virtual Switching Solution (VSS) capabilities – it seems that perhaps Cisco internally believe that to have Nexus with VSS would put it in direct competition with the 6500 VSS solution, and well, we can’t have that, can we? So Nexus gets Virtual Port-Channel (vPC) instead which when you think about it is really a more complex solution, although quite effective in its own way.
In reality, we’ve seen similar happening over the last few years in particular between the Business Units owning the development of the 6500 and 7600 chassis. The 6500 BU is Enterprise focused; the 7600 BU (the guys that figured by adding the word “Router” to a 6500 you could sell it to Service Providers) are entirely focused on the SP market. It was no problem having two basically identical chassis with different numbers until they started to diverge. Time was when you could run ‘enterprise’ code on a 7600 and SP code on a 6500 – perfect if you had a mixture of the two platforms. Then the great split happened, and the Enterprise code now notes when it finds itself on a 7600 chassis and barfs at you; and the same in reverse. The RSP720 supervisor came out and only runs on the 7600 while the VSS Supervisor (VS-SUP720-C) shows up for the 6500 only, supporting VSS. This kind of split might not matter to you if you have a homogeneous environment. On the other hand if you have a mixture of 65/7600 hardware, this split is devastating. Service module support for the 7600 is also not the same as the 6500 any more, so best hope you have the right platform for your business needs going forward or you may find yourself stuck at a dead end in terms of IOS upgrades.
So why would Cisco then – allegedly – create a Nexus 7009 and 7006 chassis, if not to encourage a forklift upgrade of the 6506 and 6509 chassis?
It’s also interesting to see some of the half-way implementations of protocols so far in NXOS. When will Nexus support full MPLS VPN capabilities for example? VRF Lite, no problem. And ok, the Nexus runs BGP, but it doesn’t have the kind of functionality and flexibilty you get with regular BGP on a CRS-1 running IOS-XR. Or is that the point again? Can’t have one product treading on another’s toes? It seems that this is all too common a story where Cisco tries to ensure that one BU doesn’t claim market share owned by another BU – which makes perfect sense for Cisco itself, but I have to wonder whether it’s such good news for the end user. I’d be interested in hearing your opinions on this subject as well.
But I digress…
The Trainer
I’m not going to name him or discuss him here; it really wouldn’t be fair now, would it? 😉 Suffice it to say that he knew his stuff and I enjoyed his insights into the Nexus platform.
Conclusions
DCNI-2 is a well thought out class and of high value if you are deploying the Cisco Nexus line of switches. It’s nice to see that it is being updated as new hardware and features appear (the last course I attended had a number of differences to this one).
Bottom line: if you have a Nexus and have not taken this class, you absolutely need to – and quickly!
Disclaimer: I’m publishing this on Thursday night, and there’s still a day of the course to go. There’s a tiny chance that my opinion might swing 100% on the last day. But somehow I doubt it. 🙂
Updated 2011-05-20: Updated experience printing the eKit content.





Leave a Reply