
Weird looking poodle, right? *coughs* With the recent SSLv3 Poodle vulnerability being disclosed, there has been a rush to disable SSLv3. But if you manage quite a few web sites, how can you quickly check whether or not you are vulnerable? Better still, if you know you have vulnerable sites, wouldn’t it be nice to be able to check before and after your mitigation attempts in order to confirm that SSLv3 has indeed been disabled?
The consequences of disabling SSLv3 is another discussion entirely; let’s assume that I’ve decided it’s worth disabling.
So that was my problem, so here’s what I did about it.
Poodle Poop
What I did was to write a script. In Python.
Regular readers will recall that my “go to” language is Perl, so the fact that I chose to write the tool in Python says, well I don’t know exactly what, but I’m sure it says something. I am not by any means a Python programmer, but I believe I have the tool working, and it’s pleasantly fast. I suspect that the code it won’t look right to a Python programmer, and will look comfortingly uncomfortable to perl programmers. It’s pretty much my first “proper” program in Python, so I’m going to give myself lots of leeway on this stuff.
Github
So that you can both laugh at the code, try it out if you like, and hopefully help me improve it, I’ve put my SSLv3Checker code on github. For all its failings, and there are many, I’ve been able to check long lists of hosts remarkably quickly using the tool, and it’s easy to spot the failing hosts with “XX” in the output. For example:
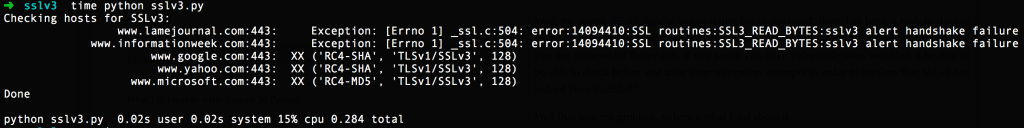 The output is unapologetically widescreen and a handshake failure means that the server refused SSLv3, which is a good thing. This is quick and dirty at its quickest and dirtiest, but it’s functional. And at <0.3 seconds to check 5 websites, I’m not unhappy.
The output is unapologetically widescreen and a handshake failure means that the server refused SSLv3, which is a good thing. This is quick and dirty at its quickest and dirtiest, but it’s functional. And at <0.3 seconds to check 5 websites, I’m not unhappy.
Did I do anything hideously bad in the code? Am I actually reading the output incorrectly and it isn’t working at all? Did you give it a go? Just fork and clone the repo and you can give it a shot. If it’s useful, that’s nice. If not, well it was useful to me, so pthththtp!
If you had a similar situation with SSLv3, how did you do your pre-/post-testing?
30 Blogs in 30 Days
This post is part of my participation in Etherealmind’s 30 Blogs in 30 Days challenge.

Leave a Reply