I suspect all of my readers are well aware of the Spectre exploit affecting, among others, Intel CPUs going back many years. Intel for their part, after a few missteps, have issued microcode updates for more recent CPUs. But for those of us with computers running older CPUs, the solutions are less likely to be forthcoming. Thankfully there is a solution.

Branch Prediction and Speculative Execution
The Spectre exploit affects processors which perform branch prediction, a kind of optimistic lookahead where the processor prepares and executes a potential instruction before it is actually requested. For example, if the processor encounters conditional code (like and if..then..else construct), based on previous behavior it predicts what the most likely outcome is and thus which branch of code would be executed as a result, then loads and executes that code in advance (hence “speculative execution”). If the branch prediction is correct, then since the code was already executed the code will benefit from improved performance. Spectre abuses some predictable timing behavior of the speculative execution to be able to extract other processes’ data from the CPU caches. In other words, it’s bad news for security.
The only way to restore security is to disable branch prediction on the CPU, but that’s something that can only be achieved by reprogramming the CPU (it’s not a selectable BIOS option, for example). In terms of patched microcode, priority has of course been given to more recent processors, leaving those of us with machines still running older processors in a bit of a bind. The good news is that there is a solution for processors launched prior to the 2nd Generation Core processor series.
Spectre Mitigation Method
While the microcode software patch disabling branch prediction and speculative execution is not available for all processors, it turns out that it is possible to physically disable branch prediction on older CPUs. Control for branch prediction has been tracked down to single pin on the CPU package and removal of that pin will prevent the branch prediction (BP) code from execution.
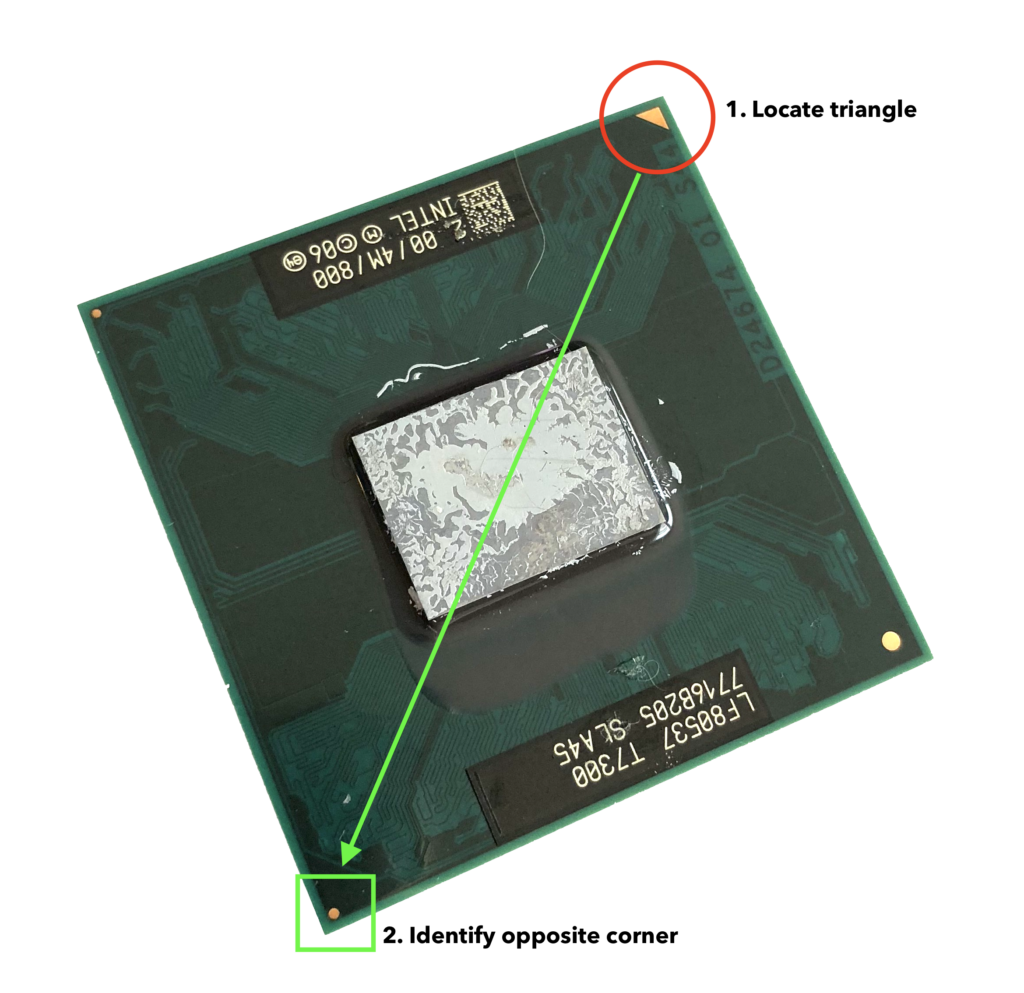
Step 1. Get Correct CPU Orientation
Remove the CPU from the motherboard and look for the triangle which has been silk screened on top of the cpu package in one corner (red circle on diagram). Take a note of the corner diagonally opposite to that triangle (green square on diagram):
Step 2: Locate BP Pin
Noting the corner identified by the green square above, turn the CPU over so that you the pins are facing upwards. The BP Pin is the pin located on the very outside of the CPU package in that corner:
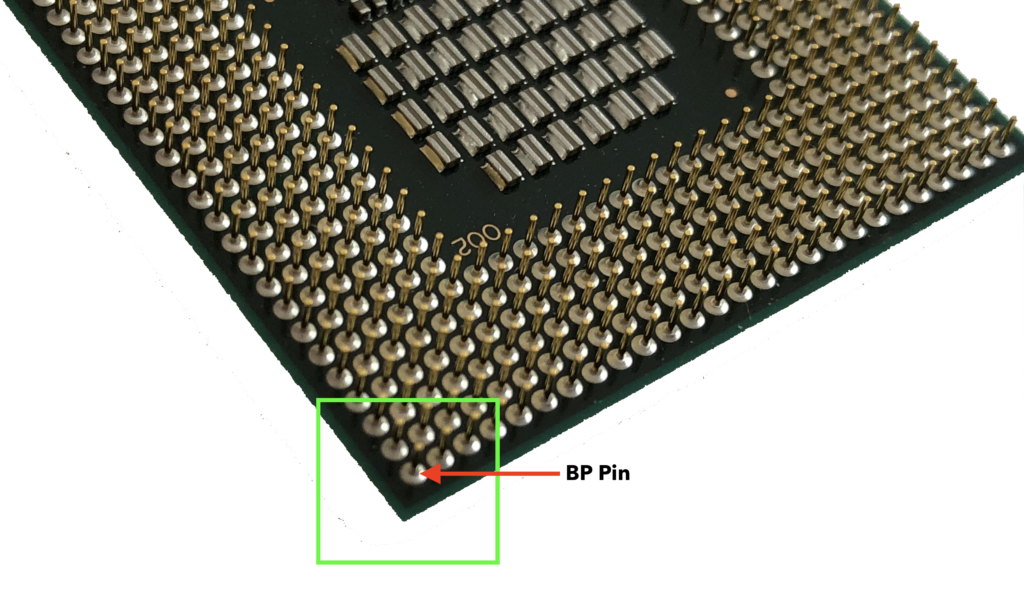
Step 3. Remove the BP Pin
Using side cutters or sharp scissors, remove the BP Pin from the CPU:
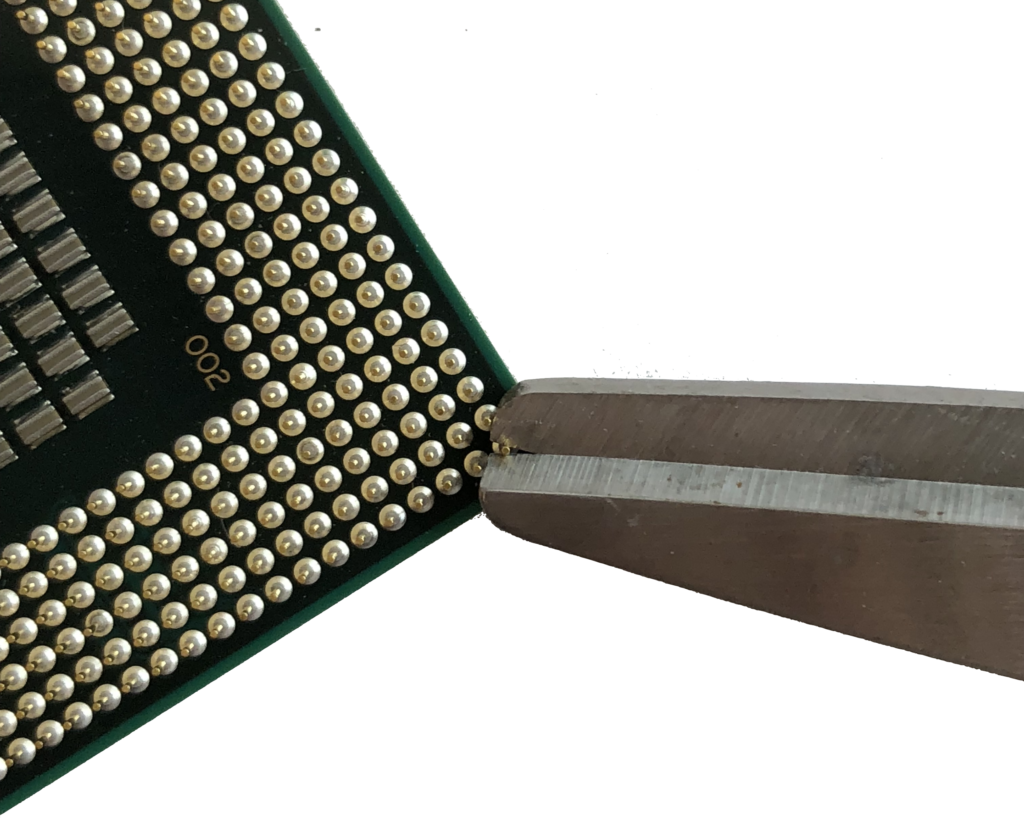
Step 4: Check Pins
After removing the BP pin, check that no other pins have been bent or damaged, and straighten them as necessary:
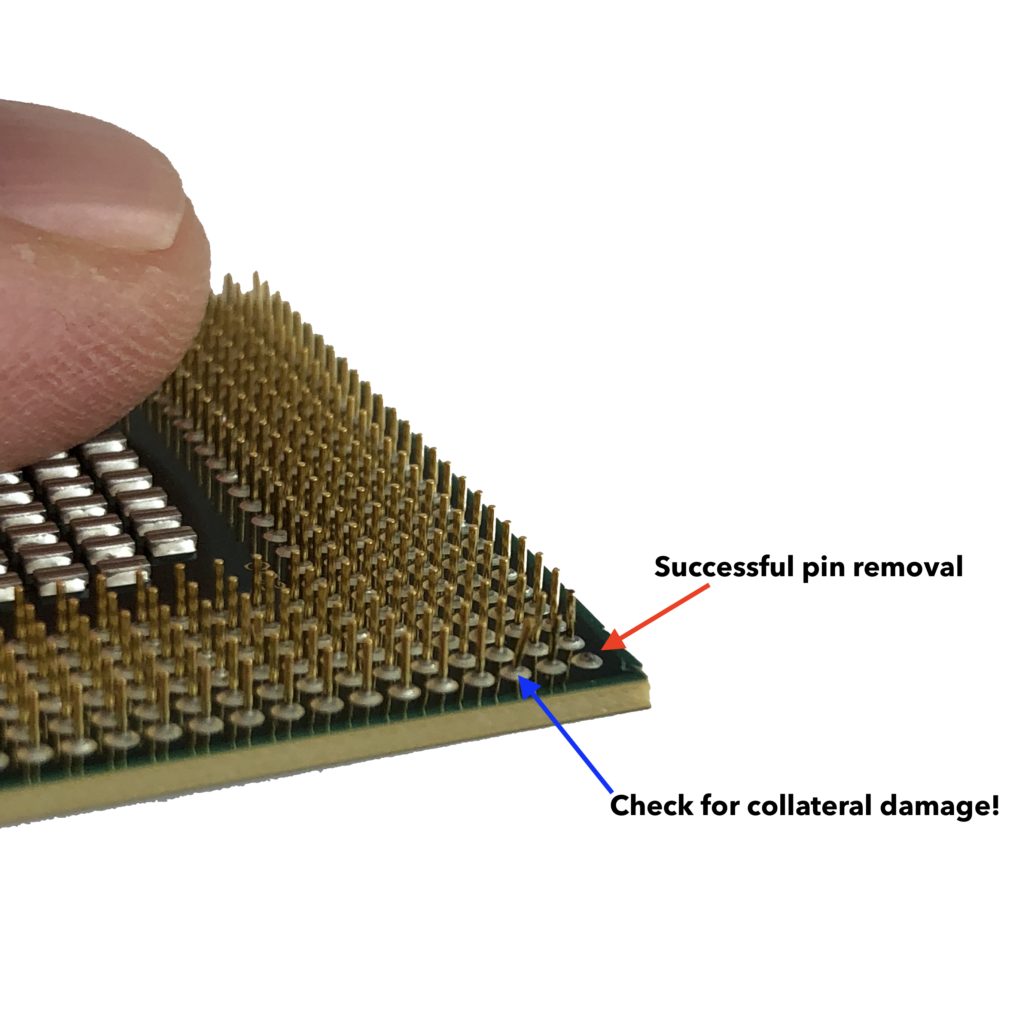
Step 5: Re-install CPU
The CPU can now be reinstalled. If the motherboard BIOS has an advanced CPU settings page, it may also display the Branch Prediction setting as Unavailable
or Disabled
. If so, this would confirm that the modification has been successful.
Step 6: Revel In Your New-Found CPU Safety!
Congratulations!
Liability Disclaimer
Instructions given on this page are for educational purposes only, and MovingPackets.net is not advising you to make this modification. Any decision to modify your CPU is yours, and yours alone; if you choose to do so, you do so at your own risk. MovingPackets.net accepts no responsibility or liability for any damage or loss, direct or indirect, as a result of replicating these steps on your own CPU.
And yes, of course this is an April fool’s post. Don’t be silly now.

Have you cut the pin on your CPUs?
Of course, I have to stay safe, Mark!