Skyport Systems offers a trusted computing platform to securely host virtual machines. Big deal? Well, maybe more than it seems at first glance.

I was sitting in some Juniper training last week being told about their Zero Trust security capabilities (referred to in VMWare NSX terminology as micro-segmentation
), and as I listened I started thinking about zero trust
in the wider context of who can be relied upon when it comes to software, and even the hardware on which it runs.
Software Issues
Let’s face it, the events of the the last few years have brought to light for Americans that far from a need to fear what other nation states might be willing to do to get access to our data, the real threat may lie within. Juniper was in the news at the end of last year after the announcement that ScreenOS contained unauthorized
code suspected of being planted there by the NSA. And then in January 2016, Juniper announced that ScreenOS would be dropping the NSA-developed Dual_EC_DRBG random number generator which perhaps coincidentally has a known weakness in it, a vulnerability that was made even worse by an implementation change in ScreenOS to use a larger cryptographic nonce length. Both threats meant that a third part may have been able to spy on traffic that was supposed to have been encrypted and secure.
Hardware Issues
The Snowden leaks, for example, have revealed the lengths to which the NSA will go to infiltrate both software and hardware, including intercepting shipments of servers and network equipment during shipping and implanting their own firmware before shipping it on to the destination. Even if you can fix the software issues, the hardware might be corrupted from the get go. How on earth do you get a secure platform on which to run your business?
The Hardware Threat
We actually put a surprising amount of trust in hardware, and especially in our x86 compute resources and network connections. We just assume that the Network Interface Card (NIC), for example, is not capable of caching data and/or sending it to a third party. We use encryption acceleration hardware yet we assume that it operates securely and does not have backdoors that would expose the unencrypted data. We assume that the server BIOS and ILO interfaces do not give backdoor access to the underbelly of our systems.
On top of this potentially questionable platform, we then obsess about the software we put on it, running anti-virus software, anti-malware software, IDS/IDP software, encrypting our hard drives, patching the OS and applications as quickly as possible when they are released (which is sometimes after an exploit has been, well, exploited). And then virtualization came along, so now we have another layer of software which has the potential ability to provide access to absolutely everything in the platform via the VM’s hardware emulation.
If we take this a step further, what if compromised hardware is used to run an SDN Controller? It’s feasible that a malicious third party might have the ability to reprogram an entire network from a host that is trusted by the network components.
Detecting Problems
With all this going on, how do we detect problems? It would be nice to have logs that would show evidence of surreptitious activities, but as any good rootkit author knows, the first thing you do is to intercept all the key system calls and ensure that your own presence and activities are hidden from view. Logs held on systems that are potentially insecure are unreliable witnesses.
Skyport Systems
Skyport Systems sees their products playing a key role in fixing at least a portion of this problem. Skyport offers a trusted computing platform that attempts to eliminate issues from the bottom up, because a secure system sitting on insecure hardware is effectively an insecure system. The product has a hardened hardware / software stack, a Security I/O Co-Processor, and TPM (Trusted Platform Module). The idea is so abstract security execution from application execution by providing a trusted hardware platform running Xen hypervisor on SElinux using Single Root Virtualization (SRV).
Skyport starts at the hardware layer, auditing the server hardware’s chain of trust all the way back to the source to make sure that the hardware provided has not been tampered with. Skyport’s Security I/O Co-Processor is then added to the mix to continuously monitor hardware and software integrity and generate its own tamper-free transaction logs independently of the software running on the server.
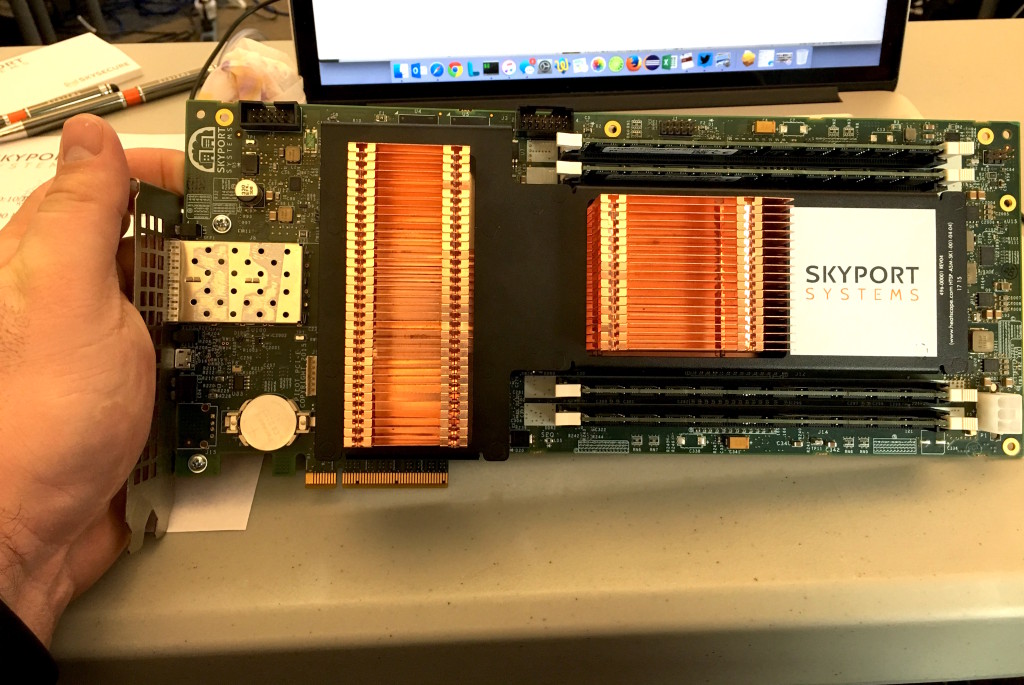
The Security I/O Co-Processor (pictured above) is interesting. All network flows, even between VMs on the platform, go through this network card; there is no soft-switching for VMs. This allows the Co-Processor to monitor all traffic and log all activity, even when it would not normally have left the hardware platform. The I/O Co-Processor can also perform a few other interesting functions, including:
- hold private keys so that they don’t have to be stored within a VM;
- filter what traffic gets put on the wire based on domain name and zone-based access;
- proxy web apps and crypto;
- proxy credentials (this one’s interesting: the credentials
known
by a VM are locally significant and may not be what is actually sent to the end system. If those credentials are somehow obtained, they’re useless for a direct connection to the other machines because what’s known locally is not the real credential); - identity management proxy;
- administrative access control (ssh, vnc, rdp proxy, secure web console);
- file system and content filtering.
Zero Trust Model
All of the above effectively implements a wildly enhanced version of zero-trust security on top of a zero-trust hardware platform. The current sales model is that of a service offering; at the time of asking, $2500/month gets a ready to deploy hardware platform described as being equivalent to 8-10 AWS M3 Large servers, remotely managed by Skyport Systems. After around 36 months (typical contract length), the hardware will be refreshed upon renewal.
This isn’t going to be something that will be deployed for every server in a data center; it’s just not feasible. On the other hand, I can’t help thinking that this would be a really sound idea for some key systems. My thoughts are for example:
- Authentication systems (radius, tacacs, etc.)
- SDN controllers
- Active Directory controllers
- Virtual security devices (e.g. firewalls)
As paranoia about security continues to increase, this platform is here to fill a gap; a niche gap, but a critical gap. For the highest security elements in the data center, it makes a lot of sense to consider a platform that not only protects the platform itself but wraps around it and controls outgoing and VM-to-VM traffic as well.
Networking Field Day 11
Skyport Systems presented at Networking Field Day 11 (NFD11), and it was reassuring that this company is driven by some pretty well known names in the industry, such as Doug Gourlay, and founders Rob Rodgers, Will Eatherton and Michael Beesley, and a personal favorite, the inimitable Lisa Caywood.
Since there’s no way I can do justice to the product in a short post, I’ve linked to the NFD11 videos below. This really is an interesting idea, and I can see the value proposition for the kind of key systems I mentioned above, and I’m sure, many more.
Zero Trust
Zero Trust? The more I learn, the less trust I have in everybody and everything. The obvious problem, of course, is that if I rely on Skyport Systems to provided a trusted platform, I have to trust Skyport Systems instead, and how much can I trust them and the security of their own code? I’m sure you can guess their answer, but if you go down this path I recommend asking just that question and seeing how you feel about the answer you get. Based on what I heard, I think you’ll be fairly impressed.
NFD11 Videos
Introduction to Skyport and SkySecure with Doug Gourlay
Doug Gourlay Discusses Skyport Systems SkySecure
Breaking the Kill Chain Demo with Dan Backman of Skyport Systems
Skyport Systems Executives Discuss SkySecure
Disclosures
I was an invited delegate to Network Field Day 11, at which Skyport Systems presented. Sponsors pay to present to NFD delegates, and in turn that money funds my transport, accommodation and nutritional needs while I am there. That said, I don’t get paid anything to be there, and I’m under no obligation to write so much as a single tweet about any of the presenting companies, let alone write anything nice about them. If I have written about a sponsoring company, you can rest assured that I’m saying what I want to say and I’m writing it because I want to, not because I have to.
You can read more here if you would like.

Its probably a company funded by the NSA. 🙂